Tuesday, December 26, 2023
Thursday, September 21, 2023
Thursday, July 27, 2023
subdomain vhost code
_________________________>>>>><<<<<_____________________
replace sub.mritsolotion.com to your subdomain name.
sudo mkdir /var/www/sub.mritsolotion.com
sudo chown -R $USER:$USER /var/www/sub.mritsolotion.com
sudo chmod -R 777 /var/www/sub.mritsolotion.com
sudo chmod -R -f 777 /var/www/sub.mritsolotion.com
nano /var/www/sub.mritsolotion/index.php
sudo nano /etc/apache2/sites-available/sub.mritsolotion.com.conf
ServerAdmin webmaster@localhost
ServerName sub.mritsolotion.com
ServerAlias www.sub.mritsolotion.com
DocumentRoot /var/www/sub.mritsolotion.com
Options FollowSymLinks
AllowOverride all
Require all granted
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
sudo a2ensite sub.mritsolotion.com
sudo systemctl reload apache2
_________<<<<<>>>>>___________
Saturday, March 25, 2023
How to Change Skin Color from Dark to Light in Photoshop[ Step by Step ]...
Do you want to learn how to change your skin color from dark to light using Photoshop? In this tutorial, we'll show you an easy and effective way to achieve a lighter skin tone in your photos.
Throughout the tutorial, we'll offer tips and tricks for achieving a natural-looking and realistic result, without sacrificing the original features and characteristics of the subject.
By the end of this tutorial, you'll have a solid understanding of how to change skin color in Photoshop and be able to apply these techniques to your own photos. So, grab your computer and join us on this journey to enhance your photo editing skills!
==============================================================================
Here is photoshop tutorial you may watch
==============================================================================
-----------------------------------------------------------------------------------------------------------------------------------------------------------
.
Sunday, March 19, 2023
How to Remove Anything from an Image using Photoshop [Step-by-Step Tutor...
In this tutorial, you will learn how to remove anything from an image using Photoshop. we'll guide you through the process step-by-step, so you can achieve the best results. We'll cover everything from selecting the area you want to remove with the Lasso Tool.
Follow along and take your photo editing skills to the next level!
Wednesday, December 2, 2020
develop web application in PHP codeigniter
I will develop all type of Web Applications based on your requirement such as Business Application, E-Commerce, E-Learning, Account Solutions, Custom Websites, Software's according to PHP MVC & Software Architecture.
VIEW
Thursday, December 24, 2015
How to Remove Snap.do Search from Chrome, Firefox, IE
Hello guys
This is another useful video tutorial How to Remove Snap.do Search from Chrome, Firefox, IE by Minhazurnetwork. In this video I show how do get rid form Search.snapdo.com Browser Hijacker virus. If you search on google you find many remover software to remove this virus but first you need to buy them. If you watch this video and flow the sample step you can get rid from this kinds of virus. So watch this video and enjoy.
If this video helpful to you please like and share this video on youtube. If any question Please comment us. And Please subscribe your channel on youtube.
Wednesday, December 9, 2015
How to change background Image in Photoshop
Here is my another useful Photoshop tutorial how to change background image using Photoshop. In this tutorial I am show how can use Photoshop selecting tools an how use to use it when you need it.how can i change the background image and create a new one I am show in this video tutorial you can easy to learn. Please watch my video tutorial and If you think it a helpful tutorial for you then you subscribe my youtube channel and keep update on every tutorial in my channel. Thank you. see you on my youtube channel
Sunday, November 29, 2015
How to fixed Error Apache shutdown unexpectedly
Some time's Apache server show an error its say Error: Apache shutdown unexpectedly. This may be due to a blocked port, missing dependencies, improper privileges, a crash, or a shutdown by another method.Press the Logs button to view error logs and check the Windows Event Viewer for more clues If you need more help, copy and post this entire log. Every new user first time face this error and they try to out of this error.In this tutorial I am show how to solve the Apache shutdown unexpectedly.If this tutorial help to you please subscribe my channel on youtube.
Monday, November 23, 2015
How to Whiten Teeth in Photoshop. Photoshop Tutorial
Photoshop is a powerful Photo editing software. In this tutorial how to whiten teeth in photoshop I am showing some photoshop tool that build your photos more effective. you just follow my instruction that i show in this video below.if you need more photoshop tutorial video you watch my channel on Youtube
Monday, November 9, 2015
how to remove clothes in photoshop tutorial
Photoshop Healing brush tool is use for retouching and repairing Image and text.However, the Healing Brush tool also matches the texture, lighting,
transparency, and shading of the sampled pixels to the pixels being
healed. As a result, the repaired pixels blend seamlessly into the rest
of the image.
The Healing Brush tool can be applied to video or animation frames.
In this tutorial I am show how to remove clothes using the healing brush tool. I Think this Photoshop tutorial help you to work whit healing brush tool.watch my tutorial and follow this instruction to learn how to use healing brush tool in photoshop.If you like my tutorial Please subscribe my channel on youtube
The Healing Brush tool can be applied to video or animation frames.
In this tutorial I am show how to remove clothes using the healing brush tool. I Think this Photoshop tutorial help you to work whit healing brush tool.watch my tutorial and follow this instruction to learn how to use healing brush tool in photoshop.If you like my tutorial Please subscribe my channel on youtube
Wednesday, November 4, 2015
How to set auto bleed in Photoshop
Now I am show you how to set bleed in Photoshop. we know that Photoshop is a vary powerful photo editing software. we are use this tool different ways.this Photoshop tutorial make this easy and quick way to use bleeding tools. You just watch my tutorial and follow my instruction. I hope this tutorial help the graphic designer and all the Photoshop use to edit their photo. lets watch my video. If this video help you and you like Please subscribe my youtube channel.
Wednesday, September 16, 2015
How To Fix: The Hosted Network Couldn’t Be Started Problem
Today I fascinating another network error in Windows 8. The error says “The hosted network couldn’t be started. The group or resource is not in the correct state to perform the requested operation“.
There are problem with hosted network adapter that not working
properly. So I’m trying some fixes to solve this error and finally found
the solution. So here I give you a step that working for me and now my
network is working fine. So follow simple steps to solve the hosted
network couldn’t be started issuing in Windows 8.
if you think you can solve The Hosted Network Couldn’t Be Started problem watch my video on youtube and follow my instruction.
If any problem please send me a command or message me on youtube or my bloge
Friday, July 31, 2015
How to Create Visitor Counter using PHP and Mysql
You might have seen visitor counter on many websites.
Visitor counter is a simple script which is used to show number of visits on
your webpage. This Post will explain you the simple code to create your
own visitor counter using PHP and Mysql. You can use this code in any of
your web applications to keep track on your visitors number in database
for analysis
Just Follow Two Simple Steps to create your own visitor
counter using PHP and Mysql in your Web application
- 1. Create a Table in your database
- 2. Create a test file to implement the code (counter.php)
Step 1: Create Table in your database
Simply make a table with name
tbl_counter(any name) in your database to keep the records of visitors.
CREATE TABLE `tb_counter` (
`counter` INT( 11 ) NOT NULL AUTO_INCREMENT ,
PRIMARY KEY ( `counter` )
) ENGINE = MYISAM ;
Step 2: Create a php file (Test File)
<?php
session_start();
require_once 'db_con.php';
$counter='';//initilize counter
$sql="SELECT counter FROM
tbl_counter";
$resultc=mysql_query($sql);
$rows=mysql_fetch_assoc($resultc);
$counter=$rows['counter'];
// if count is empty
if(empty($counter)){
$counter=1;
$insertCounter="INSERT INTO
tbl_counter set counter='".$counter."'";
$result1=mysql_query($insertCounter);
}
// increment visitor count
$increasecounter=$counter+1;
$sql2="update tbl_counter set
counter='".$increasecounter."'";
$result2=mysql_query($sql2);
?>
<!DOCTYPE HTML>
<html>
<head>
<title>
Hits Counter
</title>
</head>
<h1>
<?php echo "Total hits in this page=" .$counter ; ?>
</h1>
</html>
To know more watch my video tutorial in you tube to know more
Monday, July 13, 2015
How to Create a Javascript confirmation button
A confirmation box is used to let the user make a choice. A confirmation box will appear will with an "OK" button and a "Cancel" button. Different actions will occur depending on what button the user clicks. You can specify this course of action with conditional logic. A confirmation box can be displayed using Javascript's confirm() function.
Syntax:
confirm("Text
to display in the confirmation box");
Here is a Example :
<html>
<head>
<script type="text/javascript">
function checkdelete()
{
var chk=confirm("Are you sure delete This ?");
if(chk){
return true;
}
else{
return false;
}
}
</script>
</head>
<body>
<form>
<input type="button" onclick="return checkdelete();" value="Click me for some reason" />
</form>
</body>
</html>
Thursday, July 2, 2015
How to Remove Shortcut Virus From Your Computer Laptop Pen Drive Flash Drive Memory Card
How to remove shortcut virus? Now a day it a common question for us. If your file is infected by it, it will be hidden and inaccessible until at some point that it becomes corrupted and unusable. Not good, right?
I created this ultimate guide on how to remove shortcut virus and other important things that you need to know about this virus. To make you aware about it and be able to protect your devices against it. I am creating a video about How to remove shortcut virus form your computer. you can see this video and easily remove shortcut virus form your computer Laptop Pen Drive Flash Drive or memory card.So let’s start.
I created this ultimate guide on how to remove shortcut virus and other important things that you need to know about this virus. To make you aware about it and be able to protect your devices against it. I am creating a video about How to remove shortcut virus form your computer. you can see this video and easily remove shortcut virus form your computer Laptop Pen Drive Flash Drive or memory card.So let’s start.
Sunday, October 27, 2013
How to set up a VPN in Windos 7, Step by step setup a VPN connection
What is VPN?
A Virtual Private Network (VPN) is a
network technology that creates a secure network connection over a public
network such as the Internet or a private network owned by a service provider.
Large corporations, educational institutions, and government agencies use VPN
technology to enable remote users to securely connect to a private network.
A VPN can connect multiple sites
over a large distance just like a Wide Area Network (WAN). VPNs are often used
to extend intranets worldwide to disseminate information and news to a wide
user base. Educational institutions use VPNs to connect campuses that can be
distributed across the country or around the world.
In order to gain access to the
private network, a user must be authenticated using a unique identification and
a password. An authentication token is often used to gain access to a private
network through a personal identification number (PIN) that a user must enter.
The PIN is a unique authentication code that changes according to a specific frequency,
usually every 30 seconds or so.
VPN creates a tunnel, and all your network and online
activity travels through it. From the point of view of someone else sniffing
around on the same network, your activity is hidden because it is inside that
tunnel. Furthermore, all your data is encrypted, giving you another level of
security.
There are
two types of VPN connections: incoming and outgoing. An outgoing session means
the user is using the computer to remotely connect to some other network or
machine, as may happen when the user is accessing a work computer. If you have
a wireless router at home that supports VPN, you can set up an outgoing
connection from your laptop to connect to the router and get access to your
media server, your home computer, and other devices on your home network
remotely.
An incoming
session means other machines can access your machine. Think carefully before
you grant access to your computer. One scenario where this makes sense is if
you have a lot of media files or documents on the computer that people need to
be able to access at any time.
It is straightforward to set up
either type of connection using the built-in VPN client in Windows 7
Step by step setup a VPN connection:
1. Go
to Network and Sharing Center (under Control Panel, Network and Internet), then
go "Set up a new connection or network. click on "Connect to a
Workplace" in order to start the connection wizard, and then select
"Use my Internet connection (VPN)" option to begin the process.
 |
| minhazurnetwork |
2. In the Internet address field,
enter the IP address of the VPN server or the network's domain name. This
information will usually be provided by the network administrator. If you are
connecting to the home router, then you would put in the IP address of that
router.
The
destination name field displays the name users would see. If you aren't going
to connect right away, select the "Don't connect now; just set it up so I
can connect later" checkbox.
Leaving it
unchecked means the client will try to make a connection at the end of the
wizard. If there are multiple users on the Windows 7 box, you can either check
off "Allow other people to use this connection" to make the VPN
connection available to others, or leave it unchecked to ensure no one else has
the option.
 |
| minhazurnetwork |
3. This screen asks for a username and
password. If you leave it blank, you will be prompted to enter the information
when making the actual connection.
4. The final window, if you selected
"Don't connect now," will display a "Connect now" option.
You can close the window now, or connect.
When you are
ready to connect, just click on the network icon in systray (the icon could be
for the wireless network or for the wired one) and the connection that was
created earlier would show up in the list under "Dial-up and VPN."
You can also get here by clicking on "Connect to a network" under
Network and Sharing Center.
5. In the VPN connection box, enter
the username and password to the VPN network, if it isn't already
pre-populated, along with the domain provided by the administrator. This
connection should work for a majority of VPN networks.
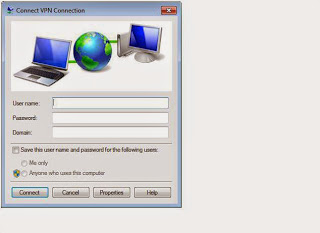 |
| minhazurnetwork |
6. If the
connection fails, click on Properties. The most common issue has to do with the
server configuration. Select the "Security" tab in the Properties
window. Type of VPN" should be set to Automatic. Check with the
administrator if it should be set to PPTP, L2TP/IpSec, SSTP, or IKEv2. If it
still doesn't work, it's possible you should uncheck "Include Windows
logon domain" under the Options tab.
 |
| minhazurnetwork |
7. After
saving the properties, select Connect to launch the connection. You are now
connected to a VPN server and your connection is safe.
Wednesday, June 12, 2013
Google Penguin,The difference between Penguin and previous updates,Google’s Penguin feedback form
Google Penguin is a code name for a Google algorithm update that was first announced on April 24, 2012. The update is aimed at decreasing search engine rankings of websites that violate Google’s Webmaster Guidelines by using now declared black-hat SEO techniques, such as keyword stuffing, cloaking, participating in link schemes, deliberate creation of duplicate content, and others. Unlike PageRank, however, Google makes all updates to this algorithm public.
Naming the algorithm update
The Penguin update went live on
April 24, 2012. However, Google did not announce an official name for it until
two days later.Penguin’s effect on Google search results
By Google’s estimates, Penguin affects approximately 3.1%
of search queries in English, about 3% of queries in languages like German,
Chinese, and Arabic, and an even bigger percentage of them in "highly
spammed" languages. On May 25, 2012, Google unveiled another Penguin
update, called Penguin 1.1. This update, according to Matt Cutts, was supposed
to affect less than one-tenth of a percent of English searches. The guiding
principle for the update was to penalize websites using manipulative techniques
to achieve high rankings. The purpose per Google was to catch excessive
spammers, but it seems some legitimate sites and SEOs have been caught with
this latest algorithm change. Few websites lost search rankings on Google for
specific keywords during the Panda and Penguin rollouts. It appears anchor text
was to blame in these cases, as the links pointing to these sites concentrated
on only one or a few keywords while the content of the websites was
satisfactory. As the update focused on the quality of backlinks, so the result
varied for different websites. Some sites lost rankings for everything while
some sites lost rankings on only specific keywords. One affected site had too
many doorway pages with city/state pages. Google specifically mentions that
doorway pages, which are only built to attract search engine traffic, are
against their webmaster guidelines. Regardless, many people still use this
technique. Penguin 3 was released Oct.
5, 2012 and affected 0.3% of queries. Google internal team uses different
numbering for its Penguin updates despite what others are calling them.
The difference between Penguin and previous updates
Before Penguin, Google released a series of algorithm updates called Panda with the first appearing in February 2011. Panda aimed at downranking websites that provided poor user experience. The algorithm follows the logic by which Google’s human quality raters determine a website’s quality.
In January
2012, so-called page layout algorithm update was released, which targeted
websites with little content above the fold.
The
strategic goal that Panda, Penguin, and page layout update share is to display
higher quality websites at the top of Google’s search results. However, sites
that were downranked as the result of these updates have different sets of
characteristics. The main target of Google Penguin is spamdexing (including
link bombing).
Google’s Penguin feedback form
Two days
after Penguin update was released Google prepared a feedback form, designed for
two categories of users: those who want to report web spam that still ranks
highly after the search algorithm change, and those who think that their site
got unfairly hit by the update. Google also has a reconsideration form through
Google Webmaster Tools for the 700,000 sites. Matt Cutts explained that over
600,000 of them were about black hat and less than 25,000 about unnatural
links.
Saturday, June 8, 2013
Google Panda Panda process Panda algorithms Panda recovery between Panda and previous algorithms
Google Panda
is a change to Google's search results ranking algorithm that was first
released in February 2011. The change aimed to lower the rank of
"low-quality sites" or "thin sites", and return
higher-quality sites near the top of the search results. CNET reported a surge
in the rankings of news websites and social networking sites, and a drop in
rankings for sites containing large amounts of advertising. This change
reportedly affected the rankings of almost 12 percent of all search results.
Soon after the Panda rollout, many websites, including Google's webmaster
forum, became filled with complaints of scrapers/copyright infringers getting
better rankings than sites with original content. At one point, Google publicly
asked for data points to help detect scrapers better. Google's Panda has
received several updates since the original rollout in February 2011, and the
effect went global in April 2011. To help affected publishers, Google published
an advisory on its blog, thus giving some direction for self-evaluation of a
website's quality. Google has provided a list of 23 bullet points on its blog
answering the question of "What counts as a high-quality site?" that
is supposed to help webmasters "step into Google's mindset".
The Panda process:
Google Panda
was built through an algorithm update that used artificial intelligence in a
more sophisticated and scalable way than previously possible. Human quality
testers rated thousands of websites based on measures of quality, including
design, trustworthiness, speed and whether or not they would return to the
website. Google's new Panda machine-learning algorithm was then used to look
for similarities between websites people found to be high quality and low
quality.
Many new
ranking factors have been introduced to the Google algorithm as a result, while
older ranking factors like PageRank have been downgraded in importance. Google
Panda is updated from time to time and the algorithm is run by Google on a
regular basis. On April 24, 2012 the Google Penguin update was released, which
affected a further 3.1% of all English language search queries, highlighting
the ongoing volatility of search rankings.
On September
18, 2012, a Panda update was confirmed by the company in its official Twitter
page, where it announced, “Panda refresh is rolling out—expect some flux over
the next few days. Fewer than 0.7% of queries noticeably affected"
Another
Panda update began rolling out on January 22, 2013, affecting about 1.2% of
English queries.
Significant differences between Panda and previous algorithms:
Google Panda
affects the ranking of an entire site or a specific section rather than just
the individual pages on a site.
In
March 2012, Google updated Panda and stated that they are deploying an
"over-optimization penalty," in order to level the playing field.
Panda
recovery:
Google
says it only takes a few poor quality, or duplicate content, pages to hold down
traffic on an otherwise solid site. Google recommends either removing those
pages, blocking them from being indexed by Google, or re-writing them. However,
Matt Cutts, head of webspam at Google, warns that re-writing duplicate content
so that it is original may not be enough to recover from Panda—the re-writes
must be of sufficient high quality. High quality content brings
"additional value" to the web. Content that is general, non-specific,
and not substantially different from what is already out there should not be
expected to rank well: "Those other sites are not bringing additional value.
While they’re not duplicates they bring nothing new to the table.".
Subscribe to:
Comments (Atom)




